Perimeter Intrusion Detection Systems (PIDS) can be a key part of an overall physical security plan, offering highly effective, cost-effective protection.
Perimeter intrusion detection systems (PIDS) can be a key part of an overall physical security plan, offering highly effective, cost-effective protection. For the system to be a success, especially when deployed at remote and unmanned sites, it must meet the following requirements:
- Reliably detect and deter would-be intruders
- Avoid complacency by minimizing nuisance alarms
- Be cost-effective for smaller, remote sites
- Offer scalable integration options, with support for existing security, communications, and/or SCADA networks
Detect intruders at the perimeter — before they get inside!
The first step of any security plan is to deter intruders. Fences provide a physical barrier but these can easily be bypassed. An effective security system communicates to intruders that their presence is known, they are being watched and response forces may already be dispatched.
Senstar perimeter intrusion detection sensors turn existing fences into smart fences, detecting and locating attempts to cut, climb, or lift the fence fabric. They are field-proven, difficult to defeat and work reliably in rain, snow, and wind. Senstar video analytics complement the sensors by providing the ability to detect and track people and vehicles both inside and outside the perimeter.
When an intruder is detected, the generated alarm (which includes intrusion zone or precise location) can be used to trigger other on-site security resources, including PTZ cameras and deterrent devices like sirens, loudspeakers, or security lights. The system can be monitored by centralized security personnel, enabling them to assess the situation remotely and dispatch a response if required.
Senstar’s newest product, the Senstar LM100 Hybrid Perimeter Intrusion Detection and Intelligent Lighting System, includes built-in capabilities to deter intruders. Highly configurable, its perimeter lights can be set low (e.g. 30-percent intensity) during nonevents in order to reduce light pollution and electrical usage. When an intruder is detected, the lights can instantly switch to full intensity as well as strobe the luminaire nearest the intruder. In addition to providing uniform illumination along the perimeter for on-site cameras, the intelligent lighting acts as a profound psychological deterrent.
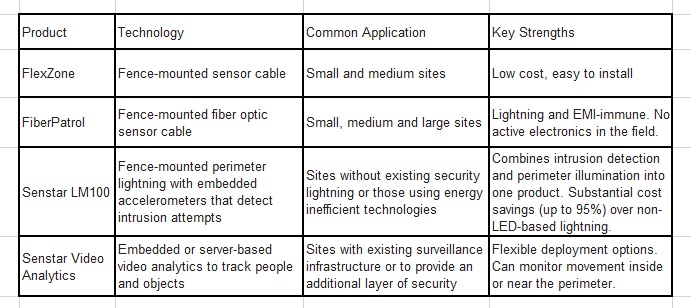
A comparison of Senstar perimeter intrusion detection systems
The following table provides a quick comparison of FlexZone, FiberPatrol, the Senstar LM100, and Senstar Video Analytics systems:
Enhance security while minimizing capital and operational costs
The additional security provided by an intrusion detection system far exceeds that of its cost.
- Fence-mounted systems are only a small fraction of the cost of the fence itself.
- The Senstar LM100 reduces electricity consumption and maintenance costs by as much as 95 percent when compared to perimeter lighting from traditional security lighting technologies.
- Analytics-based intrusion detection leverages the investments already made in the surveillance system
- Fewer security incidents and/or insurance claims
- Reduced nuisance alarms and precise ranging data leads to fewer and shorter on-site visits.
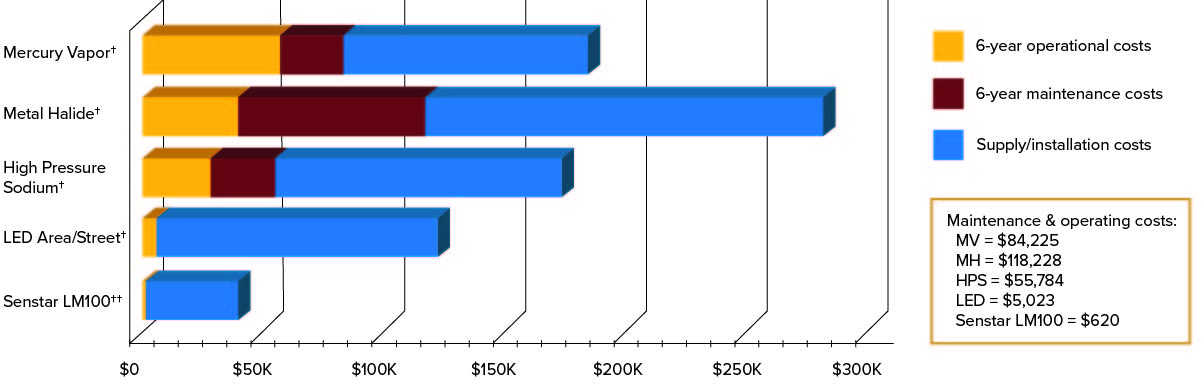
The maintenance and operating costs of the Senstar LM100 versus other perimeter lighting solutions.
Electricity cost assumes 11¢/kWh.
† Based on 30-foot lighting standard used for HPS, MH, MV and LED area lighting.
†† Civil cost at $20/hour for installation.
Scalable solutions that maximize existing investments
Depending on implementation and budgetary considerations, security directors may choose to implement security enhancements in stages. It is critical that security devices offer scalable, cost-effective solutions that maximize existing investments.
Senstar equipment uses common protocols and interfaces, so that additional sensors may be added while preserving existing investments. In addition, the equipment is designed to minimize infrastructure requirements.
- FiberPatrol offers an extended coverage distance with no in-field components.
- FlexZone can transmit power and communications over the sensor cables to simplify inter-device communications and wiring.
- The Senstar LM100 uses an encrypted wireless mesh network for communication between luminaires.
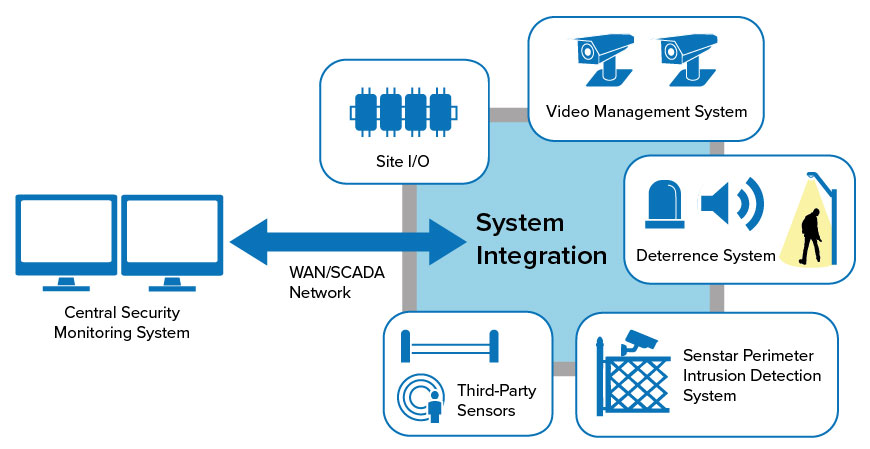
Integrate with on-site and remote security monitoring systems
Senstar sensors can be integrated with a variety of security systems, including on-site alarm panels, a security management system (SMS), a video management system (VMS) and/or a SCADA control system.
- Hardware I/O: Events and alarms are mapped to general purpose I/O collectors or alarm panels.
- Generic event interface: Events are summarized by Senstar Network Manager software and transmitted to the head-end via an open interface (e.g. ASCII text over serial, UDP, or TCP/IP).
- SDK with full API: All Senstar products include a robust, field-tested API that enable sensor integration with industry-leading Senstar and third-party security and video management systems.
Conclusion
Site operators need perimeter security solutions that are reliable, minimize nuisance alarms, are cost-effective, and that easily integrate into their existing security systems and networks. Senstar products meet these requirements, providing field-proven detection and deterrent technology.
To find out more about Senstar, click here.