Modern technology is continuously evolving. All our data is now transmitted through the internet and the need to protect our data is essential as cyberthreats grow.
Modern technology is continuously evolving. All our data is now transmitted through the internet and the need to protect our data is essential as cyberthreats grow. Data encryption is a technology that has gained popularity due to its ability to convert information to a code, which prevents unauthorized access. The technology is especially helpful with the cyber problems we face today, which addresses the privacy concerns and data protection demands from users.
Shure network audio encryption

Shure has considered the unique security needs of our customers and developed technology to safeguard content without compromising audio quality.
Shure Network Audio Encryption uses AES-256 crypto technology to protect confidential content. The AES-256 encryption algorithm has been adopted as one of the safest forms of network protection by leading financial institutions, government bodies and healthcare services. Only Shure devices with the correct pass phrase will permit audio to be heard. With Shure Network Audio Encryption enabled, Dante audio is encrypted before being sent over the network. When it is received by another Shure device that supports this feature, it is decrypted and forwarded for IntelliMix processing or analog conversion.
Key features
- Safeguards confidential content without compromising audio quality
- AES-256 crypto technology
- Utilizes a user-configured passphrase on each device
- Can becombined with other network security measures to create multilayered security solution
- Available with Microflex Advance Ceiling and Table Array microphones, the IntelliMix P300 Audio Conferencing Processor, and selected Audio Network Interfaces
VdoCipher secure video streaming
VdoCipher provides video streaming solutions for businesses to help them stre

am content on their site or app in a smooth, secure and affordable manner. The key feature is highest security from online video piracy through DRM encryption, licensing and watermarking technologies. It ensures that no downloader or hack is able to download and pirate online content. This helps portals to earn maximum revenues from their premium videos. VdoCipher serves media and e-learning enterprises from 30+ countries with its offerings.
Key features
- Encrypted streaming
- Watermarking and DRM
- Buffer retention
- Customizable player
- Analytics
- Upload from anywhere
Gemalto SafeNet ProtectApp
Gematlo’s
SafeNet ProtectApp provides an interface for key management operations, as well as application-level encryption of sensitive data. Once deployed, data is kept secure across its entire lifecycle, no matter where it is transferred, backed up or copied. Using Safenet ProtectApp APIs, both structured and unstructured data can be secured in multi-vendor application server infrastructures. SafeNet ProtectApp’s application-level encryption can be deployed across on-premises, virtual, cloud and hybrid environments.
Key features
- Apply transparent and efficient encryption to all types of sensitive application-level data across on-premises, virtual, public cloud and hybrid environments
- Works with SafeNet KeySecure to provide centralized administration of all keys and policies
- Granular access controls to ensure only authorized users or applications can view protected data
- Support for Format Preserving Encryption (FPE), including flexible key management interfaces, as well as multiple interfaces to support the full key management lifecycle
- Broad standard and interface support, including web services (SOAP and REST)
- Built-in, automated key rotation and data re-keying
Mobotix Cactus Concept
The objective of the
Mobotix Cactus Concept is to implement a multimedia cybersecurity
campaign in order to raise awareness among potential and existing MOBOTIX customers of the importance of data security in network-based video security systems and how organizations can protect themselves through cost-efficient and intelligent solutions. End-to-end encryption with no blind spots is required, from the image source via the data cables and the data storage through to the video management system on the user’s computer. Like a cactus, whose every limb is covered in thorns, all of the modules (camera, storage, cables, VMS) in the MOBOTIX system have digital thorns that protect them from unauthorized access.
Key features
- Set of built-in tools and features that allows administrators to configure each device as multi-layered approach to cyberattacks
- Uses the services of SySS to examine the security of both software and hardware
- Provides end-to-end encryption with no blind spots
Symantec information centric encryption
Symantec’s
information centric encryption protects sensitive data, wherever it is, ensuring access only to authenticated users. The solution prevents data loss by revoking user access with central monitoring and controls. Information Centric Encryption delivers strong, simple protection that follows data wherever you store, use or move it. It protects data with enterprise-strength techniques through the integration with Symantec Data Loss Prevention, Symantec CloudSOC (Cloud Access Security Broker) or Symantec Information Centric Tagging technologies. Using highly accurate data discovery engines, sensitive data is detected on premises, in cloud and mobile locations. Alternatively, users can identify and classify files and emails that contain sensitive data.
Key features
- Protects sensitive data in the hands of third parties
- Finds and deletes rogue copies
- Supports application data and a broad set of file formats to meet the needs of the user’s information ecosystem
- Keys can be stored in a customer managed Amazon Web Services account
Thales Vormetric Data Security Platform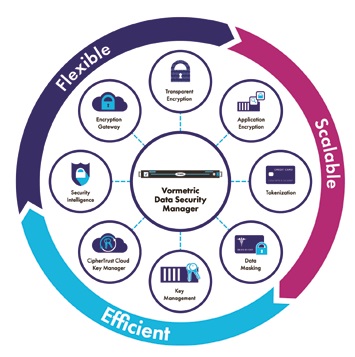
The
Vormetric Data Security Platform makes it easy and efficient to manage data-at-rest security across your entire organization. Built on an extensible infrastructure, the data security protection platform features multiple data security products that can be deployed individually or in combination to deliver advanced encryption, tokenization and centralized key management. This data security solution prepares your organization for the next security challenge and new compliance requirement at the lowest TCO.
Key features
- FIPS 140-2 compliant virtual appliance or hardware appliance
- Supports environments such as physical server, virtual server, public-private-hybrid cloud, big data, container • Encryption techniques: advanced encryption standard (AES), format preserving encryption (FPE), granular database, transparent file-level, cloud gateway
- Data pseudonymization techniques: cryptographic tokenization, random tokenization, dynamic data masking, static data masking, batch transformation
 Senetas CM7 Network Encryption Management
Senetas CM7 Network Encryption Management
Senetas CM7 Network Encryption Manager (CypherManager) is Senetas’ innovative encryption management platform. Designed as an element manager, it enables the intuitive management of the full range of Senetas CN network encryptors, across all Layer 2 Ethernet and Fibre Channel network protocols and topologies. Encryption management includes real-time status monitoring, configuration changes and certification. CM7 is a Windows or Linux-based application that loads onto a PC and uses SNMPv3 to configure, manage and monitor your encryptors. Featuring a simple, intuitive user interface, CM7 provides users with the ability to view and configure multiple devices on screen at the same time; making the configuration of endpoints quicker and easier.
Key Features
- Secure in-band and out-of-band remote management using SNMPv3
- Automatic detection and management of Senetas encryptors
- Real-time monitoring and display
- Integrated certificate authority
- Purpose-built graphical management tool