In this increasingly converged security world, the next evolutionary step is inevitably greater unification of systems and capabilitiesseamless operation back and forth between, say, access control and video. If both systems are unified into one application, the overall benefits to the end user are greater and more far-reaching than anything the market has seen up to this point.
 In this increasingly converged security world, the next evolutionary step is inevitably greater unification of systems and capabilitiesseamless operation back and forth between, say, access control and video. If both systems are unified into one application, the overall benefits to the end user are greater and more far-reaching than anything the market has seen up to this point.
In this increasingly converged security world, the next evolutionary step is inevitably greater unification of systems and capabilitiesseamless operation back and forth between, say, access control and video. If both systems are unified into one application, the overall benefits to the end user are greater and more far-reaching than anything the market has seen up to this point.
Importance of Unification
Integration means only that two products work together, while ¨unification〃 means a single, multifunctional application. A unified application includes unified security, administration, log-ins and unified responses to events, along with fully coordinated fail-over capabilities. Integrated systems require logging into the separate systems to program coordinated responses to system events. Failure to program either system properly can result in unpredictable results and neither system can detect the programming inconsistency and warn the user. Technical support teams are often not able to resolve the problems efficiently because they are not aware of the inconsistencies, thus increasing the total cos t of owner ship and system downtime.
Unity brings about greater availability to physical security. In the past, cameras were hard-wired to DVRs or matrix systems , and card readers were hard-wired to access control panels and servers with serial communications. When the host failed, these hard-wired connections prevented automated fail-overs to standby services. In the new unified systems, fail-overs are automated, because the underlying IP infrastructure permits hot standby services to immediately assume responsibilities for the failed components.
A few examples illustrate the operational potential of such unified systems:
Unified systems can automatically coordinate the reaction to changing threat levels. For example, during a period of heightened facility security, automatic card entry can be suspended and live video of personnel requesting access can be displayed in real-time. Upon presentation of an employee's access card, that person's personnel photo is pulled from the database and displayed. The guard can then manually allow or deny access to that cardholder. Whereas, the card would normally provide access, during high security periods the guard can definitively determine if the right person is using the card.
The intelligence gleaned from a unified security solution provides a wealth of statistics that can be used to illuminate and solve security challenges. We find at our facility that, on average, a particular door remains open for five seconds after a valid card is read. However, a quick check of a particular door's activity today shows three events of longer than five seconds. The security guard can click on each event to see a video of what happened, or program the system to pop video whenever the behavior for a door is out of the specified norm. Unified systems have major implications in terms of the level of security, budget, efficiency and overall capabilities. Since all system design and hardware/software choices usually start with the budget, that seems the best place to begin.
Financial Benefits

The unification of access control and digital video creates a synergy that results in the proverbial ¨1 + 1 = 3,〃 but this level of synergy is considerably greater than just three.
IP-based distributed processing allows for modular and economical system expansion. A unified system supports integration as a means of migration from legacy systems and provides a cost-effective bridge to the future. This defines a true ¨open system〃 for access control: a single platform from one vendor that can communicate directly with access control panels from multiple brands.
The unified system manufacturer ensures a consistent product version and consistent upgrade path. The end user does not have to worry if the video and access control versions will become out of sync or lose features as they would in an integrated system. Training and product support also take on a more holistic approach without requiring the end user to act as a middleman between various vendors. A unified system ensures the latest standards-based software, networking and hardware technology.
A unified system means one user interface. A single user interface simplifies installation, and is easier to learn and use. With one common interface, there is no more duplication of system administration and other tasks. For example, a user learns to set up a card reader using the same skills required to set up a camera. In addition, a single user log-in provides a simple and secure access to all security functions.
When evaluating overall system design for an integrated system, one must ask, ¨What is missing?〃 or ¨Will component A be compatible with system B?〃 A unified system eliminates the research required to determine compatibility and how many functions are available in an integrated, bolted-together system. In a unified system, all functions between access and video are compatible, eliminating the need for the end user to manage version compatibility. Unified IP systems also reduce maintenance costs seen with most integrated systems, and networking issues are handled by the IT department using standard tools and practices.
Cost Effectiveness and Efficiency
We have seen that a unified access control and IP video system has a number of cost advantages, but it also demonstrates clear advantages in terms of system efficiency as well. The system's use of existing IP infrastructure eliminates significant wiring and installation costs. IP network nodes, including cameras and card/biometric readers can all be managed by a corporate network management tool.
A single database allows for improved information correlation, so that people who are seen on the video are also identified by the access control component. Normally video could show the person, but users had no practical way of comparing what they saw against a photo or a database.
Unified system manufacturers will also have unified hardware. For example, DVTel's access panels can store video and control PTZ cameras. The system is no longer reliant on the host computers for control. This adds a level of survivability and greater efficiency, as edge devices can control both aspects of the system. As we have seen above, IP-based distributed processing allows for modular unlimited expansion based on the end user's needs and budget.
Overall Security?
What with all the talk of cutting costs and system efficiency, you might think the unified system sacrifices something in overall enhanced securityjust the opposite. The heightened security advantages from a unified system offering include:
A unified system provides highly intelligent security access control ¨anomalies〃 can trigger video and video anomalies can be used to control access.
Video intelligence can be utilized by access control to arm points based on an intelligent video event. For example, if a threat is detected by video intelligence, the system can automatically secure the facility entrances automatically without any human intervention or lengthy decision-making.
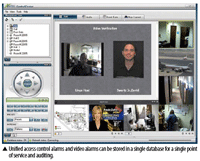
Unified access control alarms and video alarms can be stored in a single database for a single point of service and auditing.
A fully IP-based system allows access to personnel whereabouts and identity verification data when logging into an enterprise application. By applying just these few examples to the reader's own facilities, it is clear to see the many ways in which a unified system can provide unprecedented security, while also delivering greater efficiencies and superior cost-effectiveness.
Unified, Open Systems Now
Unified systems, as defined by those comprising IP-based video and access control, offer so much more than the ¨advanced〃 integrations of bolted-together components we have seen to date. Unified systems offer enormous advantages in terms of system openness and flexibility; enhanced efficiency at lower costs, and level of functionality and improved overall security not available anywhere else on the market today.