Multimodal biometrics, which combine different biometric modalities to make access control even more secure, are also gaining traction. This article takes a closer look.
This year’s access control technology survey sees high scores received by mobile credentials, where smartphones are used to unlock doors; and wireless locks, which connect wirelessly to the controller or management software, thus significantly simplifying the installation process. Multimodal biometrics, which combine different biometric modalities to make access control even more secure, are also gaining traction. This article takes a closer look.
Mobile credentials
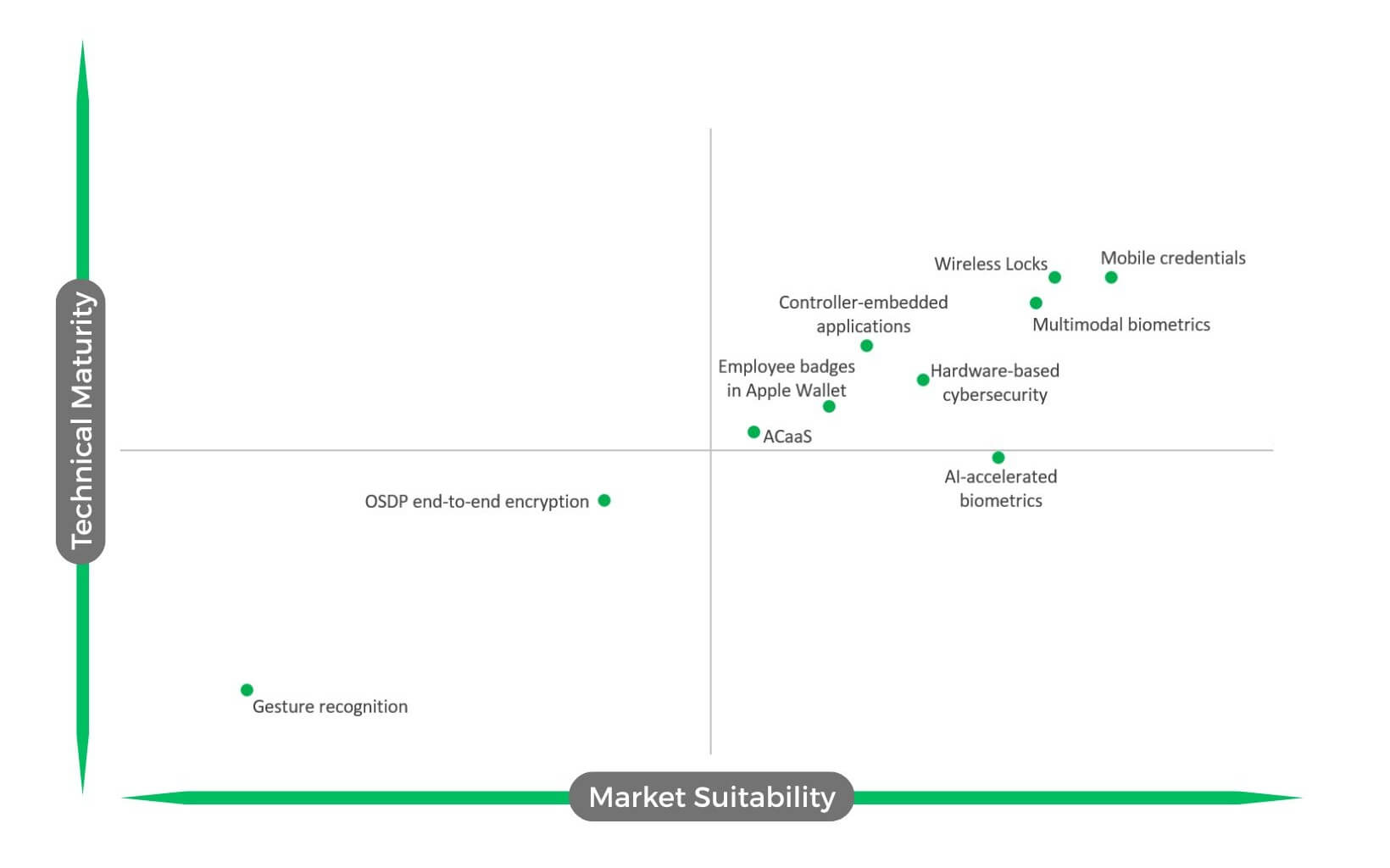
Mobile credentials have gained strong market acceptance in security over the past years. This is confirmed by our tech survey in which mobile credentials garnered suitability and technical maturity scores of 4.24 and 3.92, respectively. Indeed, the benefits of mobile credentials are quite clear. Conventional solutions such as keycards and keyfobs can be easily forgotten by users, but they almost always bring their smart devices. Making keycards and keyfobs also carries a cost, whereas mobile credentials can just be uploaded to the user’s device. At the same time, mobile credentials have also become more technically mature. The technology leverages Bluetooth Low Energy (BLE), NFC, and increasingly, Ultra-Wideband (UWB) – all of which are now supported across major mobile operating systems. Integration with digital wallets such as Apple Wallet and Google Wallet has become standardized for secure credential storage. These factors have contributed to mobile credentials’ strong growth, which is unlikely to stop anytime soon.
 Results of the 2025 access control tech survey by asmag.com
Results of the 2025 access control tech survey by asmag.com
Wireless locks
We also polled users on wireless locks, which received high scores as well. In terms of suitability, wireless locks received 4.19, while for technical maturity it received 3.92. Wireless locks are locking systems that communicate with controllers or management software wirelessly over protocols such as Wi-Fi, Bluetooth and Zigbee. This is in contrast with conventional wired solutions, over which wireless locks offer several advantages. Wireless locks allow lower installation complexity and cost, as there’s no need to run cables through walls or doors. This makes wireless locks particularly advantageous for retrofitting older buildings or heritage sites. Scalability and flexibility are another advantage, as wireless locks are easy to add, remove, or relocate as facility layouts change. Further, battery efficiency and reliability improvements have been made on wireless locks, as modern designs use low-power wireless protocols and energy-saving modes allowing batteries to last 1–3 years depending on usage and lock type. It therefore comes as no surprise that wireless locks are ranked high on our survey, and their popularity is all but certain to continue.
Multimodal biometrics
Multimodal biometrics, meanwhile, were another top scorer, receiving suitability and maturity scores of 4.17 and 3.87, respectively. Multimodal biometrics use two or more biometric modalities, for example face and finger or fingerprint and finger vein, to make access control more secure and spoof-proof.
“Multimodal biometrics, integrating modalities such as face and fingerprint, are now recognized as sufficiently mature for broad enterprise adoption. These solutions improve accuracy and anti-spoofing by combining the strengths of different authentication method. Suprema offers the world’s widest range of authentication methods and combinations, allowing organizations to create highly customized security protocols. Among these, the combination of facial authentication and mobile access stands out as both the most common and the safest approach for many enterprises. Suprema’s innovative Template on Mobile (ToM) method further strengthens security and user convenience by securely storing biometric data on the user’s mobile device, enhancing privacy and reducing risk,” said Hanchul Kim, CEO of Suprema.
AI-accelerated biometrics
Biometrics solutions provide access to users based on their physical traits such as face or fingerprint. Such solutions get a boost in performance when AI is added. In our survey, AI-accelerated biometrics scored 4.14 and 3.59, respectively, in suitability and maturity. “By combining anomaly detection with biometric authentication, operators can differentiate routine access from activity that signals elevated risk. This is a paradigm shift: from incident response to proactive intervention,” Kim said.
He adds: “At Suprema, we've been developing AI technologies internally long before the current market surge, allowing us to optimize our facial authentication devices while extending AI capabilities across our comprehensive security ecosystem. Our strategy has been to embed AI at every layer – from facial authentication and fingerprint recognition to intelligent video analytics and our unified security platform. This deep integration enables us to deliver solutions that are already field-tested and operationally proven. A prime example of our AI innovation leadership is our Financial Crime Prevention Solution, which won the 'Best of Innovation' award at CES 2025.”
ACaaS
ACaaS or access control as a service delivers access control via the cloud, allowing organizations to manage who can access what – doors, systems, or data – without maintaining on-premises servers. On our survey, ACaaS scored only moderately, with suitability and maturity scores standing at 3.94 and 3.63, respectively. Despite the moderate scoring, ACaaS will remain a viable technology due to its various benefits. Since ACaaS leverages resources in the cloud, organizations do not need to purchase expensive servers, thus seeing their upfront capital cost minimized. The technology allows scalability, enabling users to add or remove access control devices at their disposal. The technology’s ability to manage access remotely and update security policies in real time is also a draw. All these benefits make ACaaS particularly ideal for SMBs, large enterprises and organizations with multiple sites. As far as technical maturity is concerned, established cloud platforms and secure APIs are available for users to readily deploy ACaaS. Strong encryption and compliance support also makes ACaaS more secure than ever. All this puts ACaaS in a good position to see strong growth and demand in the years to come.