EWT, a Taiwan-based provider of edge magnetic/IC/RF card reader solutions for Kiosk, Vending machines, etc has revealed a series of new card readers plugged into a mobile phone or IPad increasing portability and easy access to card readers.
EWT (East Wind Technologies, Inc.), Taiwan-based provider of edge magnetic/IC/RF card reader solutions for Kiosk, Vending machines, etc has revealed a series of new card readers plugged into a mobile phone or IPad increasing portability and easy access to card readers.
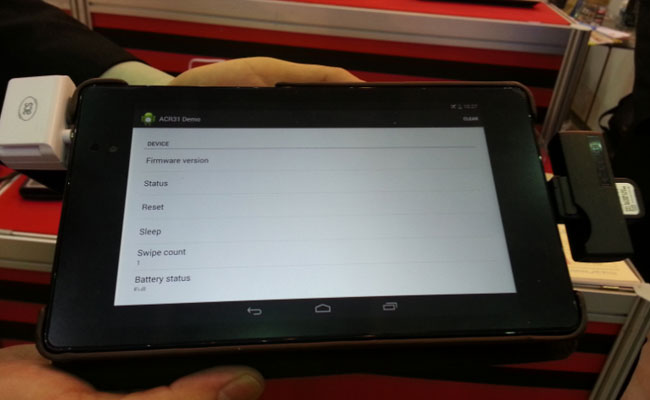
The EWTA-31 is a magnetic strip reader used to swipe credit cards as well as identity cards using the magnetic strip of these cards to identify the card holder. At events such as Secutech, it allows access to visitors by confirming identity by means of credit cards or banking cards. The software used to manage this product is an android 3.1 & iOS-5.0 application provided upon purchase. This product is attached to the mobile by means of a 3.5mm audio jack plugged into the earphone pin hole.

Similarly, the EWTA-38U-ND is an IC card reader, used in visitor management and other areas requiring identification confirmation. This device reads the IC chip used on the national health insurance cards as well as debit/credit cards. This device uses the Micro-USB port which is currently available on most if not all smart phones managed by Android 3.1/windows/Linux os.