Making sure that their connected devices are secure against cyber threats has become critical for OT.
More and more, machines on the factory floor are connected to the Internet amid the IIoT trend. While this has brought various benefits for manufacturers, it has also introduced
security risks. Making sure that their connected devices are secure against
cyber threats, then, becomes critical for
OT.
Across the globe, the
Industry 4.0 concept is gaining momentum as manufacturers leverage data generated by connected devices to achieve further automation and efficiency. In fact, according to Grand View Research, the global IIoT market size is expected to reach US$949.42 billion by 2025, expanding at a combined annual growth rate of 29.4 percent between now and that year. Growth drivers include rising demand for machine-to-machine systems and the need to contextualize OT data, according to the report.
However, with more and more OT equipment online, they are also subject to intrusion and hacking that pose a serious threat for manufacturers, regardless of the industry they work in.
“I suspect all the segments are about the same as far as vulnerabilities go,” said Ernie Hayden, Founder and Principal of
443 Consulting. “However, you need to consider which segments are highest priority for the attackers/hackers. For instance, Nation States may be after critical infrastructure whereas environmental hacktivists may be inclined to attack ‘dirty’ industries such as oil and gas processing plants, waste treatment facilities and chemical plants.”
Security often neglected
Traditionally, OT has different focuses than IT. While the latter places a strong emphasis on security, the former prioritizes production optimization and downtime reduction. Cybersecurity, then, is something that’s often neglected.
“For OT, if they haven’t encountered any cybersecurity event that brings down production or incur huge losses, when they have a set budget they are inclined to spend it on production expansion and equipment upgrade, rather than on security,” said Robert Kuo, Product Marketing Manager for IIoT Solutions at
Moxa.
Further, upgrading equipment with security features may force production to come to a halt or stoppage, which OT engineers try to avoid at all cost.
“Many OT engineers that we spoke to voiced the concern whether the added security component would affect their own system. For example, one OT engineer told us they installed an anti-virus software product, and it caused the computer to crash, and a halt to production ensued. A stoppage to production is the biggest concern for OT,” Kuo said. “A reduction in overall equipment efficiency and monetary losses – that’s what causes OT to have second thoughts about installing security.”
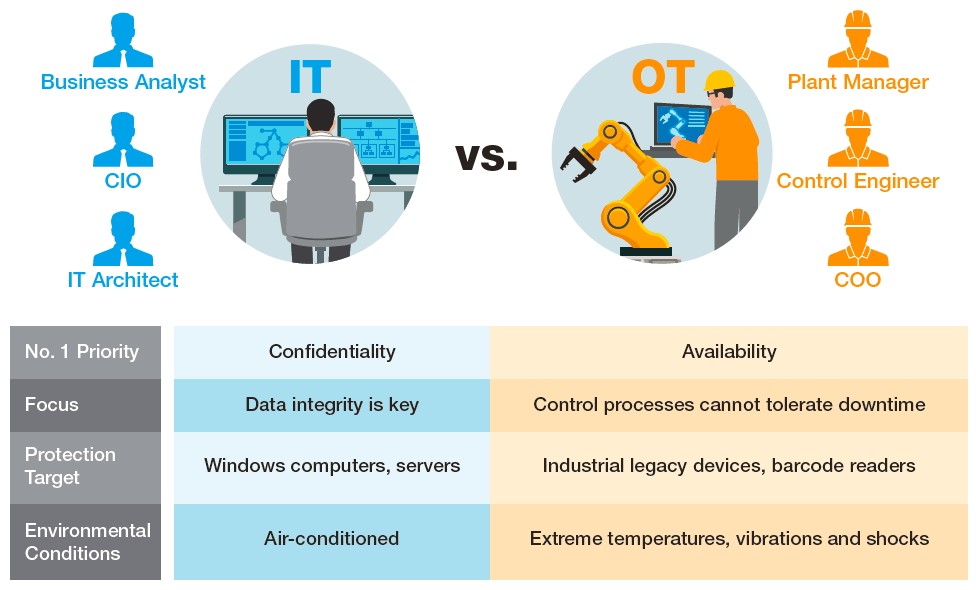 The Vast Differences between IT and OT. (Image source: Moxa)
The Vast Differences between IT and OT. (Image source: Moxa)
A joint effort
Of course, these concerns do not negate the importance and necessity of cybersecurity, which should be a joint effort between manufacturer end users and equipment vendors. According to Hayden, users can refer to certain industry guidelines, such as the North American Electric Reliability Corporation (NERC) and the Critical Infrastructure Protection (CIP) standards and the US National Institute of Standards and Technology (NIST) Special Publication 800-82 R2 Guide to Industrial Control Systems Security for best practices against cyberattacks.
For vendors, they should offer solutions that are easily understandable to OT, ensure minimum downtime and comply with international standards. The IEC 62443 standard, for example, has a subsection that requires vendors to equip their products with security measures such as account, identifier and authenticator management; password-based authentication; public key authentication; use control; data integrity and confidentiality as well as backup for resource availability.
“During the equipment selection process, choosing products that follow international cybersecurity standards is key,” Kuo said. “Our cybersecurity solutions comply with the IEC-62443-4-2 cybersecurity standard. They also have an OT-centric, user-friendly interface, which is our strong point. We also tailor our solutions to the customer’s system, so once installed, production can restart immediately.”