Access Management NFC is fully compliant with the ISO standards governing contactless smart cards. A mobile phone equipped with NFC technology can be used to carry a portable identity credential and then wirelessly present it to a reader, said Tam Hulusi, Senior VP of Strategic Innovation and Intellectual Property, HID Global (an Assa Abloy company). The phone is simply waved in front of the reade...
Access Management
NFC is fully compliant with the ISO standards governing contactless smart cards. A mobile phone equipped with NFC technology can be used to carry a portable identity credential and then wirelessly present it to a reader, said Tam Hulusi, Senior VP of Strategic Innovation and Intellectual Property, HID Global (an Assa Abloy company). The phone is simply waved in front of the reader, and the user can open the door. Based on estimates from market research firm iSuppli, manufacturers will ship approximately 550 million NFC-enabled phones in 2015.
According to SimonsVoss Technologies, two modes of access or identity management with NFC are possible.
1. As a reader (reader/writer mode):
The smartphone acts like a card reader. This allows people to read cards or tags, for example, which are small RFID chips on so-called smart posters. Tags can include web links via which people are then redirected to websites where more information on the topic is available.
2. As a card (card emulation mode):
In this mode, the smartphone is basically an access control card, adopting protocols such as Mifare Classic and DESfire. In other words, smartphones can open doors this way.
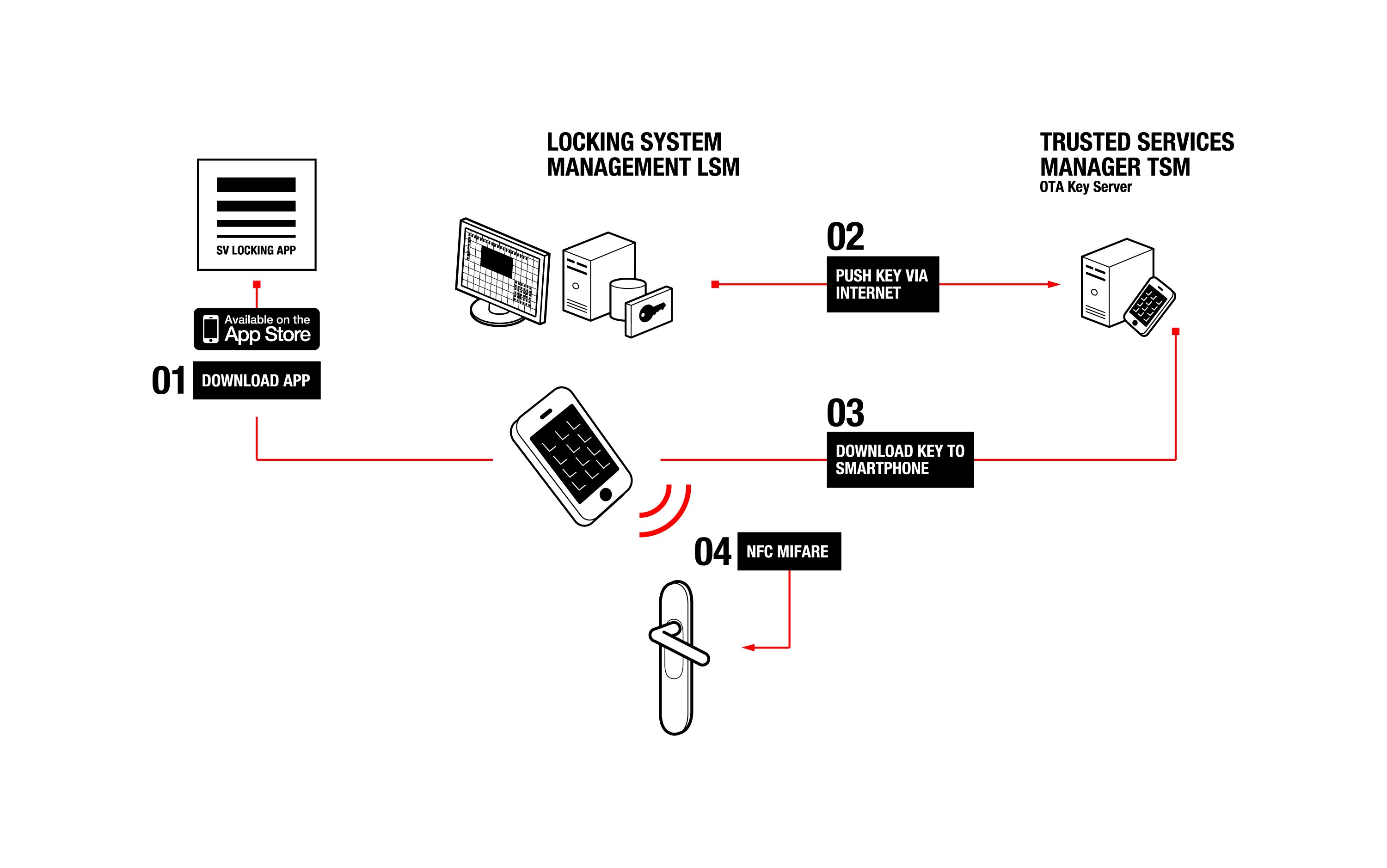
▲ Operations and mechanisms for the end user and administrator are exactly the same as before; it is just the handheld device, which used to be a plastic access card or badge, that is different now. (Image courtesy of SimonsVoss Technologies)
Smartphones can thus be furnished with access authorizations via mobile-phone networks and allow users NFC-based access to entry/exit points guarded by readers, locks, locking cylinders, smart handles and relays, SimonsVoss said in a prepared statement. In the past, facility management and maintenance personnel had to procure the corresponding keys for their duties from a key depot and return them again afterwards. With the new NFC-based key/card distribution capability, access authorizations can now be sent directly to the corresponding employees' smartphones from the headquarters at any specified time, or for limited periods of time in emergencies or replacement scenarios.
For the end user, it is as easy as downloading an app to their handset and waving it in front of a reader or lock. The system administrator simply assigns the access authorisation(s) to the user as how it was done previously: whenever something changes for a user with an NFC smartphone, a new smart card data set (Mifare Classic or DESFire) is generated automatically and pushed to a central, closed, over-the-air (OTA) key management server.
An important element for mobile access is over-the-air provisioning of digital keys and credentials to NFC-enabled smartphones. “In a hotel environment, guests receive electronic room keys on their smartphones so they can bypass the front counter when checking in,” Hulusi said, giving some real-life examples. “In a commercial environment, new employees receive their digital keys OTA so they can use their smartphones to gain access into a given building for their first day of work.”
To support these applications, a cloud-based provisioning model is advised. This will enable credential issuers to monitor and modify security parameters when needed, eliminate the risk of credential copying, issue temporary credentials as needed, and revoke credentials when devices are lost or stolen. “NFC-enabled smartphones would be very convenient and reliable universal platforms for carrying a variety of embedded keys and credentials that can be issued OTA, with improved convenience and security,” Hulusi said.
Since not all smartphone manufacturers make NFC capabilities innate yet, NFC attachments or shells are usually employed: iCartes for iPhones and microSDs for Android-based phones. These attachments, according to SimonsVoss, include an NFC chip for close-proximity communication and a secure element in which all security-critical information, such as passwords and access authorizations, are stored and cryptological calculations are performed.
Mobile Applications
Mobile wallet, file sharing, ticketing and loyalty programs are other emerging, promising NFC applications, said Jacek Debowski, Research Analyst at Frost & Sullivan. “A considerable amount of mobile-wallet applications has been introduced to the market, and Google becoming a provider of such applications is particularly noteworthy. Developers of mobile-wallet applications are actively partnering with mobile-network operators to widen the proliferation of their software and services, making mobile payment a key contributor to NFC proliferation and growth.”
Jacek Debowski, Research Analyst at Frost & Sullivan. “A considerable amount of mobile-wallet applications has been introduced to the market, and Google becoming a provider of such applications is particularly noteworthy. Developers of mobile-wallet applications are actively partnering with mobile-network operators to widen the proliferation of their software and services, making mobile payment a key contributor to NFC proliferation and growth.”
Contactless payments and contactless access control go hand-in-hand with NFC-enabled phones or handhelds; interesting “apps” also include transit ticketing, data transfers and access to online digital content, Hulusi said. This makes it easy to combine multiple virtual credentials on a single device for things like secured facility access and the ability to make cashless payments at the facility's cafeteria. “Cashless, contactless payments are becoming increasingly popular in, for example, Canada. According to an August 2010 study by Technology Strategies International, an Ontario-based tech market research firm, a significant chunk of transactions in Canadian stores will be carried out using cashless-payment systems by 2014. The value of contactless transactions is expected to reach US$5.6 billion, and there is also strong interest in mobile payments,” Hulusi said.
In Japan, NFC-based payment systems are already installed in fast-food restaurants, subways, taxis and vending machines, Hulusi continued. “University campuses would also be ideal candidates for this technology. Students can use NFC mobile phones to enter buildings, pay for parking, make purchases, use transit systems, check out library materials, identify themselves before taking tests, and access computer resources.”
Peer-to-peer exchange, such as electronic business cards, interactive games (social gaming), and Bluetooth or WLAN connections, is also possible with NFC, according to SimonsVoss.
Although several initiatives that intend to propel NFC applications are taking place, the need for investment in supporting infrastructure, which translates to ensuring larger volumes of PoS terminals and smartphones that support NFC, presently appears to be a major cause of concern for the industry, Debowski said. “In accelerating market penetration, end-user confidence and data security are significant limiting factors.”
No More “Guess Who?”
We are entering a new era of digital keys and portable, digital identity credentials that can be securely provisioned and safely embedded into smartphones. “Deploying this new model requires a seamless, end-to-end ecosystem of products and technologies for mobile keys and credentials, including the smartphones that carry them, the readers that authenticate them, the locks they open, and the services for issuing them,” Hulusi said. “With the advent of the bring-your-own-device (BYOD) business mobility deployment model, IT managers know they must protect data that is accessed by devices owned by employees and brought into the enterprise. One-time passwords or soft tokens can be generated for NFC-enabled phones or devices to securely log on to and access the network.”
Debowski added that standardization and certification efforts are being made in the industry to improve the security levels, so that trusted service providers can develop access, payment and management applications in a secured, reliable and effective manner.