Web-based access control have revolutionized the conventional way of access control. In this article, George Redpath, Director of Engineering at CEM Systems, discusses other integration that need to be taken into consideration for complete control of a building.
Web-based access control have revolutionized the conventional way of access control. In this article, George Redpath, Director of Engineering at CEM Systems, discusses other integration that need to be taken into consideration for complete control of a building.
Up until recently, access control and security fall in one of two camps. If users could afford a 24-hour manned central response center, they could reliably secure and monitor the sites within the organization. If users could not afford this, they outsourced monitoring and response to a third-party organization. This is seen as an expensive option and involves a loss of control to the user.
Now with a Web-based solution, users can reliably control and monitor security requirements even if there are multiple sites. One of the most exciting aspects of Web-based access control is the capacity of the system to be the center of an integrated solution which can manage most aspects of a small building.
This has been made possible using the new generation of intelligent devices which can support an internal Web server. These range from IP cameras to relatively simple devices, which can monitor temperatures and environmental conditions and allow the user to view activity using a device connected to the Internet. These frequently are not a classical PC but are becoming a device running Windows Mobile Software and Internet Explorer.
It is now also possible to combine a number of these devices, giving the user the impression that they are a single Web page. Such a controlling device is the webEntry II Pro system from CEM Systems. This has been available for a number of years, but is now evolving into a solution for controlling a small building.
webEntry II Pro is an access control system that is administered via a Web browser and is ideal for small- to medium-sized facilities. Using webEntry, administrators responsible for building access control can manage up to 64 doors, print ID cards, run reports and view alarms using a standard Microsoft IE Web browser on any networked PC or laptop. webEntry simply advises customers on the status of activity at their facility by sending notifications of alarms/events via e-mail, PDA or mobile phone.
In order to control a small building, the following elements are needed:
Security
Access Control
Video
Intrusion Panels
SCADA (Supervisory Control and Data Acquisition)-Based Building Control
Temperature Monitoring
Remote Input/Output
Remote Facility Alarms
Fire Alarm Status
They are arranged as shown in the following diagram (Figure 1).
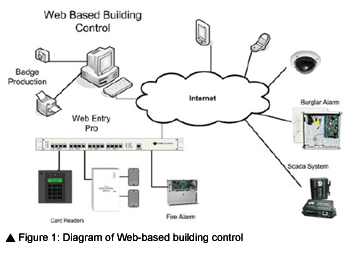
A mixture of physical contacts, embedded logical commands and use of Port Mapping implement the integration. Port Mapping works in this context, making a transparent connection from the device serving the Web page you are viewing to a second Web server utilizing different IP address and ports, in such a way that the user thinks they are still using the original Web server.
This also means that high data rate sources, such as IP video, can appear as being sourced for a low cost, low bandwidth server. This is in line with the aim of this integration, which is to facilitate real time control and configuration of a small building. It does not set out to produce a unified database of events and responses, and as a result, searching the database for an event, which occurs across the system elements, is not straightforward.
System Elements

In an ideal world, all the elements of such a system would be standards based and be easily interoperable. Unfortunately, this is not the case as each manufacturer implements their Web pages and control mechanisms in a proprietary manner. Therefore, I will set out the elements that CEM have found to work, or perhaps offer a high level of integration.
IP Camera Networks
A network camera can be described as a camera and computer combined in one intelligent unit. It captures and sends live video directly over an IP network such as a LAN, intranet or the Internet and enables users to view and/or manage the camera using a standard Web browser or video management software on any local or remote computer on a network. It allows authorized viewers from different locations to simultaneously access images from the same network camera. A small building will have a number of such cameras.
Alarm Panel Integration
Alarm panels are an important element in any small building and will probably be required to be monitored as part of the owner ˇs insurance policy. Therefore, it would be advised that in any such integration, they would still be capable of essentially stand alone operation.
Fire Alarm Integration
In this context, the integration must enable the fire panel to work totally in isolation if the Web-based control system fails. This is a more stringent requirement than the intrusion system as it is regarded as a life safety system. This may seem a contradiction but still allows for the following actions:
Command a zone to open
Receive and report the state of a local fire contact
Monitor a local glass break
Monitor the status of a zone
Thankfully, such functions are genuinely independent of the fire alarm system vendor. To suppor t this integration, the webEntry II Pro system provides four inputs and four outputs and configuration utilities to setup the triggering of fire zones, either from remote inputs or Web GUI commands.
Scada-Based Control
This is a new requirement but as we become more aware of the issues of global warming and the cost of energy, it is becoming extremely important. By integrating the energy-consuming systems of a building with the security and remote monitoring, considerable savings can be realized. Also a security system that is able to control lighting as an intruder circles the perimeter of a building gives the impression that the system is truly intelligent, increasing the likelihood of being apprehended.
Allowing for Growth
When implementing any system, it is always worth considering how the system will grow. Users need to ask themselves and any potential supplier ¨What happens when I acquire another building?〃 This question should be self-obvious but it is often overlooked. Any system should be expandable so that it can become an element in a larger global system. For this, users need a supplier who implements large as well as small systems and can handle that transition. webEntry offers the ability to be reprogrammed to become an element in a truly global system, with many users already having gone down this route as their plans and rate of development have changed.
Conclusions
Therefore, when it comes to considering a Web-based product to meet your security requirements, it should now be viewed as a method of simplifying the operation of the building, improving the way it is controlled and increasing energy and operator efficiency. This in itself will pay for the system, without considering the security benefits.
In addition, it should be expandable and when necessary reconfigurable to meet your changing needs, as these systems always grow larger and encompass new technology and interfaces.
In the dynamic environment of security and building control, the one thing which is certain is the drive to network all devices, so it is essential that the infrastructure is put in place to allow them to intercommunicate and be controlled in a coherent manner. Therefore, devices, such as webEntry Pro, should not be seen as a solution to a single problem, but a key element in the efficient management of a facility.