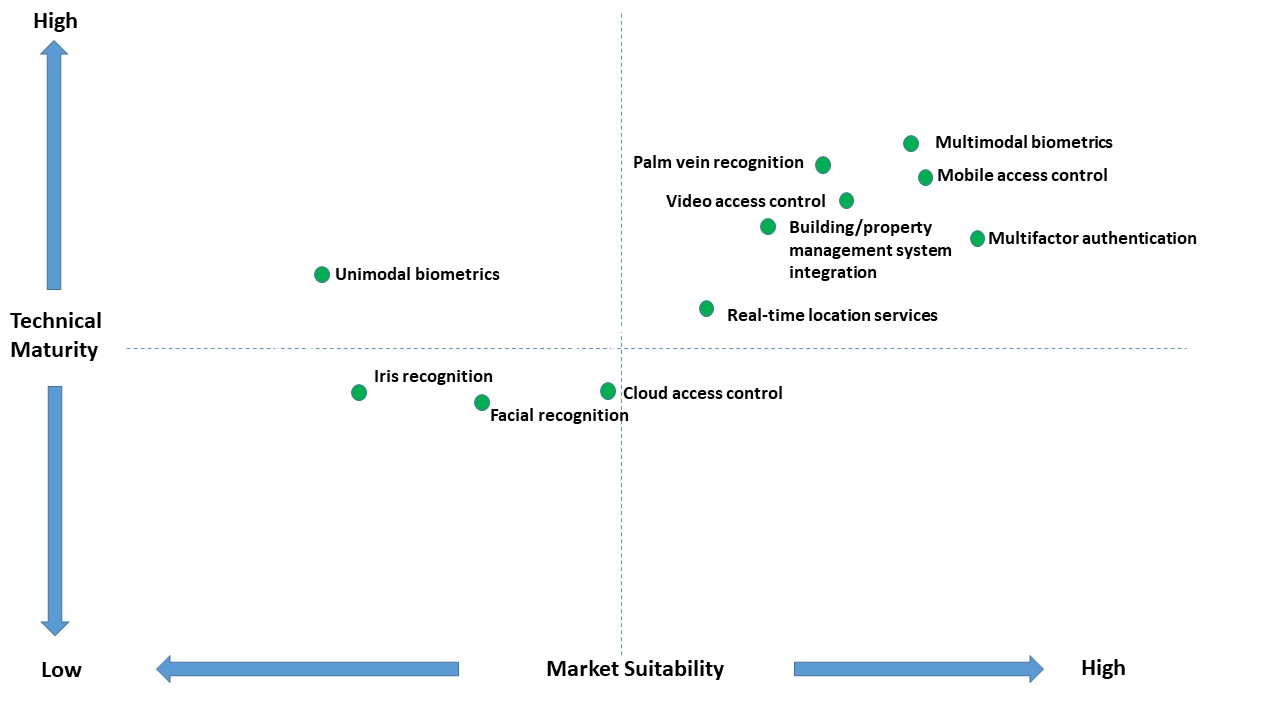
Multimodal biometrics, multifactor authentication, mobile access control, and palm vein recognition are trending.
The 2022 asmag.com access control survey of integrators, distributors, and end users showed multimodal biometrics, multifactor authentication, mobile access control, and palm vein recognition to be some of the most mature as well as sustainable technologies available now. Of these, multimodal biometrics topped the maturity ranking, while multifactor authentication was ranked the most sustainable.
We spoke to several vendors for a more qualitative response on this. While most agreed with the findings of the survey, some were able to give an in-depth perspective on consumer behavior.
The rise of mobile access control
Hanchul Kim, CEO of Suprema, pointed out that the adoption of mobile access control is growing because it is convenient, easy, and quick to use — users can just tap their smartphones and walk right through the door. It even makes it more cost-effective to manage authentication, visitors, and time and attendance of staff since there is no longer any need to issue, collect and discard physical access cards.
“Mobile access control is also highly secure: RF cards can be lost, stolen, or used by non-authenticated users, but mobile credentials are saved on an authenticated user’s smartphone, which is much safer,” Kim said. “Mobile credentials are also fully managed in the cloud, making them easy to remotely deactivate if a smartphone is lost or stolen. Suprema mobile access solutions provide all of the above features, which combine to significantly improve user convenience.”
Similar thoughts were shared by Devin Love, Senior Director for Software Products at Allegion, who pointed out that credentials stored in a user’s phone and expressed as a mobile credential will continue to be one of the most popular technologies because it works with existing paradigms for people’s lives.
“Consider this – when a biometric secure a phone, the trusted relationship and understanding of how biometric information is stored and used is already familiar,” Love said. “At the very least, it’s something the user has likely leveraged in the past. Just as important, the rapid pace of change in this area of technology can be updated through the relatively fast upgrade cycle of cell phones. While there will continue to be a variety of solutions and no one technology to rule all use cases, it can be expected that phone-based credentials will mature and be adopted at a faster rate than some others.”
 2022 Physical Security Technology Trends Reader Survey: Access Control
2022 Physical Security Technology Trends Reader Survey: Access Control
The potential of cloud-based solutions
Cloud-based solutions are becoming increasingly popular in various industries. It is popular in access control also but the wider security industry is slow to adopt it. The asmag.com survey found that most respondents gave an average rating for cloud access control in maturity and sustainability. But one company that has been focusing on the cloud as the future and advocating for hybrid cloud as the best way to transition ahead is Gallagher.
“Hybrid cloud allows for much easier deployment of a range of services,” Steve Bell, Chief Technology Officer at Gallagher Security. “Cloud allows the vendor to control software updates to always ensure that those services are always up to date and patched against any cyber risks. Implementation of a secure connection to our Gallagher cloud from the on-premise server is paramount. We always have the devices on the onsite network connect out to the Gallagher cloud as this ensures it is easy for the customer’s IT department to secure and for Gallagher to secure the connection at the cloud end.”
Gallagher’s Command Centre Web is a new user interface that uses the hybrid approach to securely allow any web browser-enabled device to run a workstation. Users can add new features to this app without any onsite upgrade, and customers will always have the latest version. In Bell’s own words, it really is the best of both worlds.
Mature solutions for broader usage
Although several access control technologies are available in the market now, many users worry about their maturity for large-scale use. Kim believes that mobile access control is mature enough to allow wider usage, mainly because mobile access control based on UWB (ultra-wideband) technology will be commercialized in the near future. UWB is an RF technology that can measure accurate distances within an error of about 5 to 10 cm.
“Smartphones embedded with UWB are being released in the market, including iPhone and Samsung Galaxy,” Kim pointed out. “The more UWB-supported smartphones are used, the more demand for mobile access control based on UWB will increase. Mobile access control based on UWB will be able to recognize users when they approach a door as long as they have their smartphone in their possession, allowing the door to open automatically with no need for further authentication. Suprema joined the FiRa Consortium, a consultative body that establishes standards for UWB, to accelerate the development of UWB-based mobile access control solutions to provide more convenient and secure user experiences.”
Others suggest that several variables limit the potential of mobile access control. Bell pointed out that while mobile access control solutions have been available for five or more years now, user experience is very dependent on using a reliable and trusted vendor. Wallet credentials will improve the performance by allowing the use of NFC on both Apple and Android. In line with the survey results, he finds multifactor authentication a mature option, although it depends on the technologies included.
“Multi-factor authentication should be used by more customers – following the lead from our computer network and internet authentication, it is important to provide the cyber protection that multi-factor provides,” Bell pointed out. “It is easy to clone most of the older credential technologies and even more recent card technologies such as MIFARE DESfire. It is still possible to steal a credential or pick up a card that somebody has misplaced. A multi-factor authentication such as a card plus PIN or card plus biometric can protect against people getting access in that way. The US Government FIPS201 standard (PIV) card has the capability for 3 factor Card/PIN/Biometric but is not used a lot in practice.”
Conclusion
The survey of asmag.com readers and interviews with vendors throw a mixed picture. But a closer look at the data shows a few clear trends for the market. For instance, mobile access control solutions are widely seen as the next big thing in access control, as the convenience and security they offer surpass most other modalities. The use of cloud-based solutions shows potential but slow growth, as both the survey and manufacturer interviews show. But given time, this could turn out to be an integral part of access control systems.
Finally, multimodal authentication is probably the most mature and popular solution across markets at the moment. This could set the stage for a smooth transition to mobile-based solutions, as mobile devices can integrate several modes of authentication within themselves.