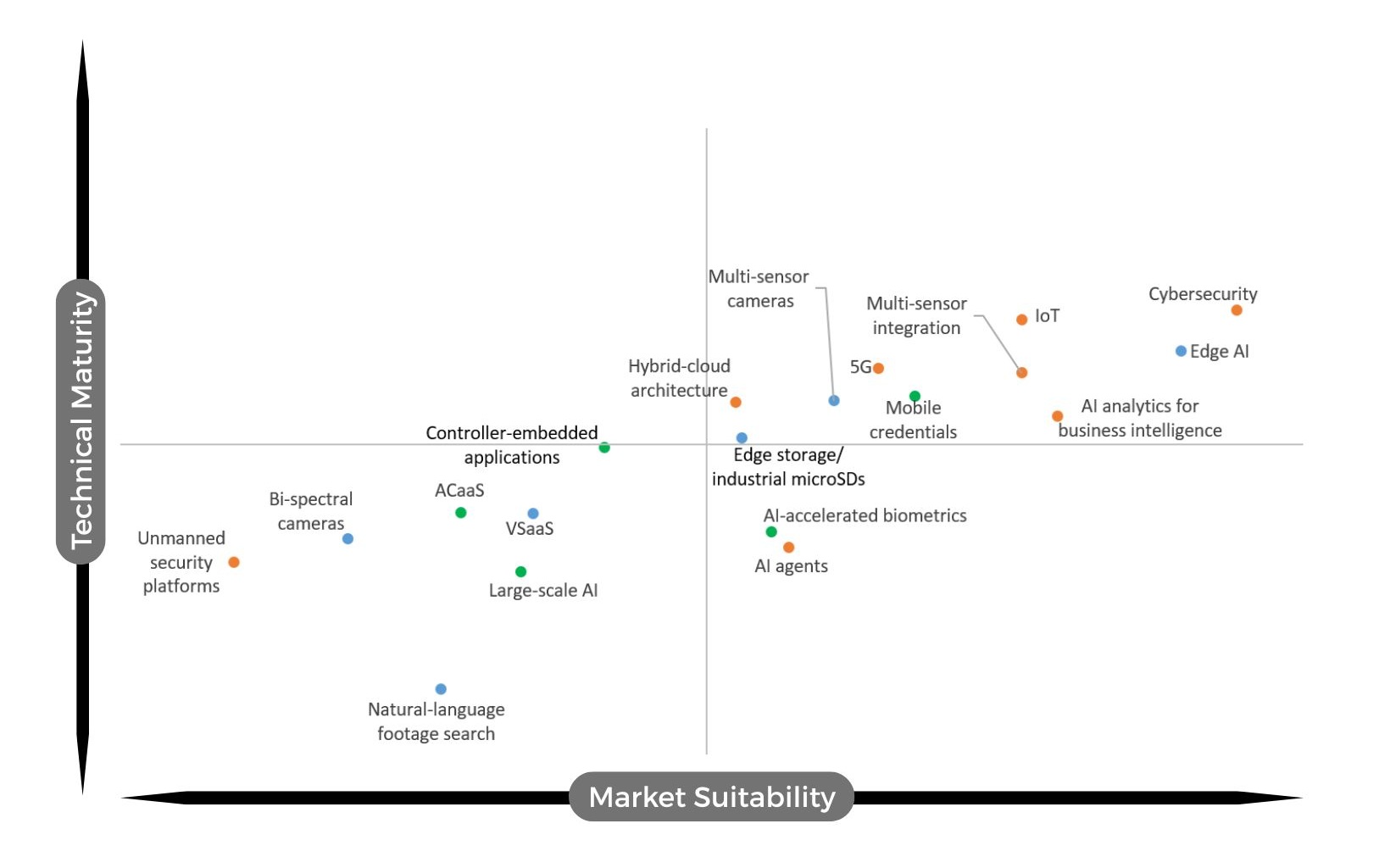
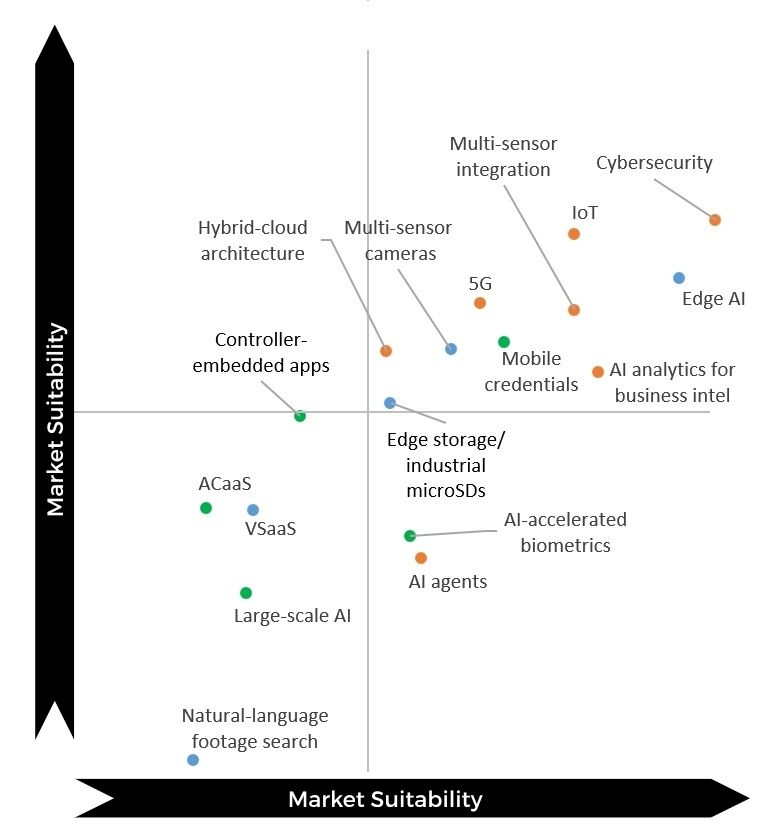
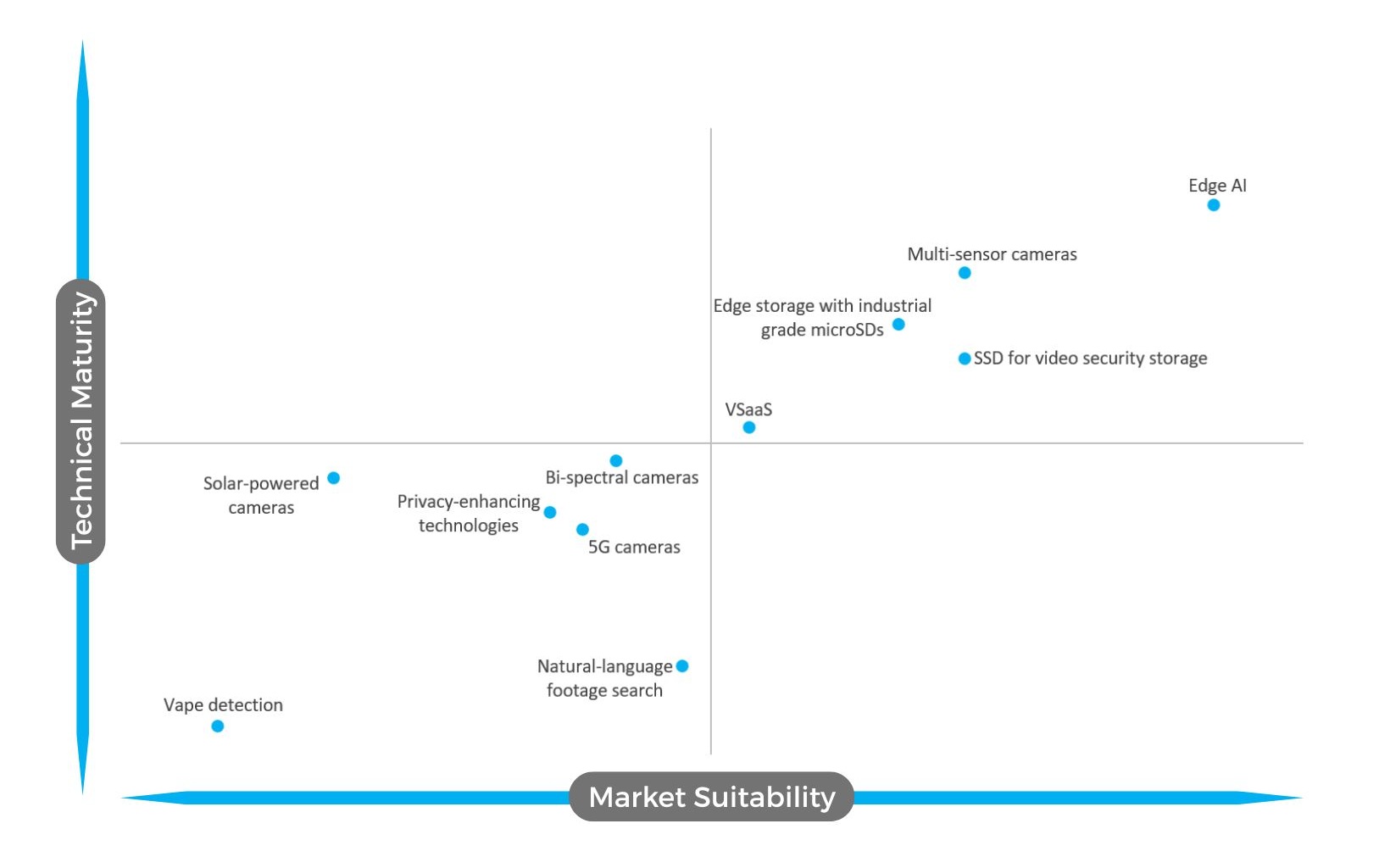
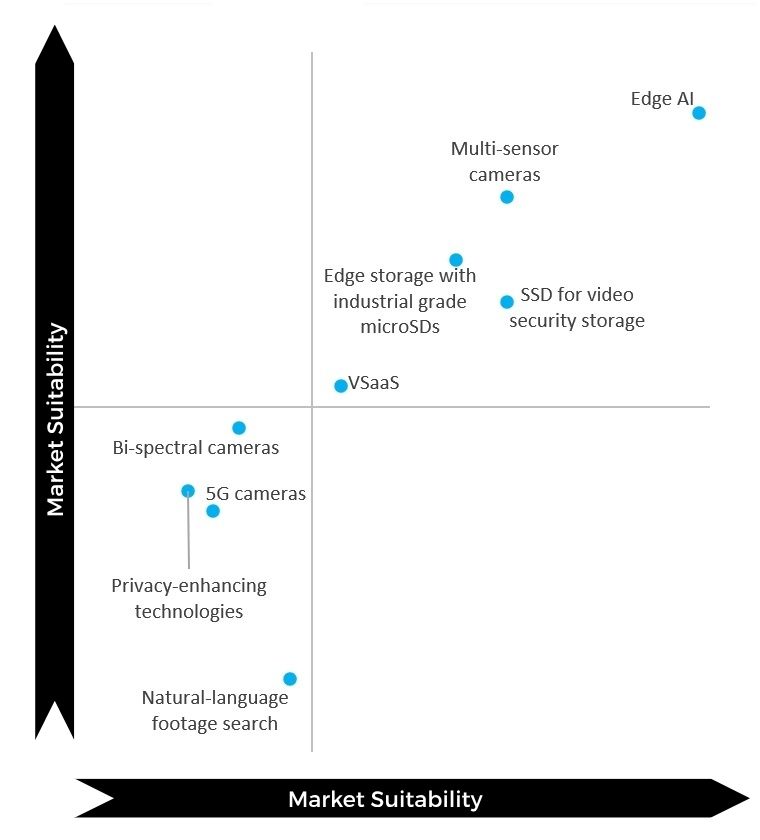
Large-scale AI, which trains on large datasets, has become one of the hottest topics in security. Especially, it is featured in various Chinese video security solutions which are claimed to provide better detection, lower false alarm rates and smarter video search. Yet in our survey, the technology only received moderate scores of 3.98 and 3.49, respectively for suitability and maturity. Indeed, being new in security, large-scale AI still sees several technical barriers that need to be overcome.
“As our experience suggest, users often perceive these technologies as not yet fully mature. One reason is the need for extensive real-world data to train robust, generalizable AI models, which is a challenge in highly variable, high-security environments. Additionally, especially in mission-critical scenarios, organizations are cautious about relying exclusively on large-scale AI until consistency and transparency are further enhanced,” said Hanchul Kim, CEO of Suprema.
Yet in the long run, the technology is expected to see increased adoption due to its benefits for users.
“Large-scale AI represents a powerful evolution in security where AI systems can learn from massive, diverse datasets across sites, use cases, and conditions. In theory, this allows algorithms to become far more context-aware and adaptive than traditional, site-specific models that are disconnected and in silos. However, in practice, we’re still in an early phase,” said Philippe Henaine, Manager of Strategic Partners at i-PRO.
He adds: “The technology itself is promising and available, but real-world integration into monitoring workflows remains complex due to factors like latency, reliability, and cybersecurity. Today, vision-language models (VLM) already transform how operators interact with video data, turning complex analytics into proactive insights. Large-scale AI models will follow, enabling cross-site intelligence and predictive capabilities once infrastructure and data governance fully catch up.”