The physical access control market has long been characterized by the “customer value equation,” a balancing act among cost, security and convenience that influence buying behavior and decisionmaking trade-offs. Validated by a recent Avisian study, this balancing act will continue over the coming years. However, there are new market dynamics that influence the interrelationship among the value equation factors, and new areas of consideration that present trade-offs as well as advantages.
The physical access control market has long been characterized by the “customer value equation,” a balancing act among cost, security and convenience that influence buying behavior and decisionmaking trade-offs. Validated by a recent Avisian study, this balancing act will continue over the coming years. However, there are new market dynamics that influence the interrelationship among the value equation factors, and new areas of consideration that present trade-offs as well as advantages.
At the heart of the data supporting these findings is the 2010 Avisian Physical Access Control Market Research report. Additionally, HID Global hosted an industry focus group of long-time integrators and senior consultants to capture real-world examples of what industry veterans find important. Finally, our findings were also in accordance with IMS Research's 2009 report, which provided additional insights.
The top five dynamics identified that influence the physical access control market include: ● Increased government influence in both the public and private sectors
● New technologies and accelerated adoption rates, including the move to contactless technologies
● Rapid adoption of multipurpose smart cards
● Growing emphasis on security requirements
● TCO and ability to invest in futureproofed solutions
While not new, these dynamics are significantly changing the customer value equation, with key marketspecific implications.
Increased Government Influence
One focus group participant expressed the sentiments of many when he said he believed government- driven standards will influence our industry more in the next three years than they have in the last three decades. Government initiatives are extending beyond the public sector to drive private-sector security implementations like never before. Many participants believed that broader government reach into the private sector will become more prevalent and cause organizations to increase their focus on security. They also indicated that while security previously was a reasonable spend and not code-driven, the US government is now targeting specific industries (such as health care, food processing, water and other public utilities) to tighten privacy standards and plans, and is even mandating secure-compound directives.
We may see this trend impact pharmaceuticals and education soon, too. It is important to note that even though the civilian infrastructure is mostly under private-sector control, governments are exerting an enormous influence in this area on physical access initiatives.
Faster Adoption
The migration to new technologies, including IP connectivity, has significant implications. According to the IMS study, IP-enabled controller revenues are expected to surpass those of serial controllers and account for 42.7 percent of the market by 2013. Driving this trend are low installation costs, reduced cabling, the desire for intelligent readers at the door, and demand for increased functionality and application convergence.
 The Avisian research identified three reader technologies that users value most highly. The first was upgradeable readers and credentials, including the ability to download reader/credential security upgrades to proactively manage threats (viewed as highly desirable by 79 percent of the respondents). The second most valued technology was upgradeable, programmable readers that would simultaneously support three or more card technologies (viewed as important by 71 percent of the respondents). The third most highly valued technology was expanded programming and configuration options, including a universal programmer and reader configuration tool for controlling credential formats and security through a supplier licensing agreement (desired by nearly two-thirds of the respondents).
The Avisian research identified three reader technologies that users value most highly. The first was upgradeable readers and credentials, including the ability to download reader/credential security upgrades to proactively manage threats (viewed as highly desirable by 79 percent of the respondents). The second most valued technology was upgradeable, programmable readers that would simultaneously support three or more card technologies (viewed as important by 71 percent of the respondents). The third most highly valued technology was expanded programming and configuration options, including a universal programmer and reader configuration tool for controlling credential formats and security through a supplier licensing agreement (desired by nearly two-thirds of the respondents).
The Avisian study respondents also said they would like a credential or identity generator to assist in defining and securing card data (desired by almost 60 percent of the respondents) and the ability to have additional credential form factors such as phones, fobs, stickers or tokens. More than 70 percent of the end-user community and 80 percent of industry respondents felt the latter capability was important, and both groups acknowledged inadequate user options today.
Even as users wait for these technologies, smart-card use continues to grow, at a 13.5-percent CAGR between 2009 and 2013 according to IMS, compared to 2.4 percent for proximity technology in the same period. IMS believes the number of smart-card installations will approach that of proximity installations by 2013. As mentioned, one of the biggest growth drivers is the desire to move to a single card or credential that can store more information for additional applications and/or security.
 Multiple Applications
Multiple Applications
To highlight the importance of multipurpose cards in the market, one focus group respondent pointed out that a major university customer will not consider any purchase unless it enables them to add more applications to existing physical access systems and credentials, or extend the use of existing applications.
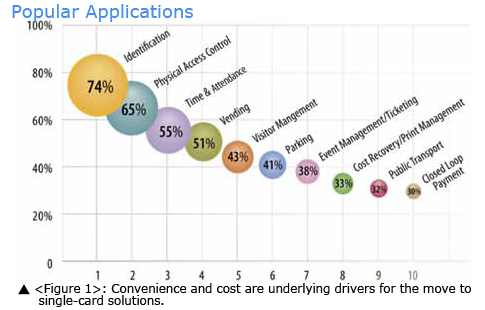
In a similar vein, 64 percent of the respondents said they felt that it was highly or somewhat desirable to store several identity formats and applications on a single credential, including identification, physical access control, time and attendance, vending and visitor management. Also ranked as desirable applications were parking ,event management or ticketing (particularly in campus environments), as well as cost recovery applications such as print management, public transit and closed-loop payment systems (see Figure 1)
Higher education and the health care sector are now moving to these multiple-application environments, and corporations are beginning to explore them, too. One example of a corporate adoption is US Bank's recent move to a single employee card that could be used for traditional magnetic-stripe purchases, contactless payment transactions and facility access. The selected technology combined Visa PayWave contactless-payment capability and iCLASS smart-card technology for physical access control and security.
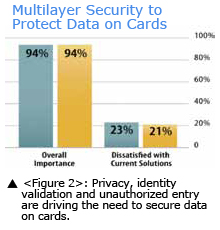 Increased Card-to-Reader Security Today's cards carry more information that must be protected, as they are used for more applications, require more privacy protection, and must be able to validate and secure identities. This has created demand for multiple layers of card security, including two-factor authentication to validate identity and biometric templates that must be stored on the card. More than 85 percent of the user community felt that this was a very important factor, and more than one‐third felt that they did not have adequate support in this area from the vendor community (which agreed). (See Figure 2.)
Increased Card-to-Reader Security Today's cards carry more information that must be protected, as they are used for more applications, require more privacy protection, and must be able to validate and secure identities. This has created demand for multiple layers of card security, including two-factor authentication to validate identity and biometric templates that must be stored on the card. More than 85 percent of the user community felt that this was a very important factor, and more than one‐third felt that they did not have adequate support in this area from the vendor community (which agreed). (See Figure 2.)
The feature that respondents said they wanted most was hardware that updates the card's security technology if the current technology were hacked. This was deemed important by 91 percent of the user respondents, and more than 52 percent were dissatisfied with today's options. The second most desired feature was software upgrades to address new security threats as they emerge, with 92 percent of the respondents saying this was important and almost 40 percent saying they were dissatisfied in this area.
TCO and Future- Proofing
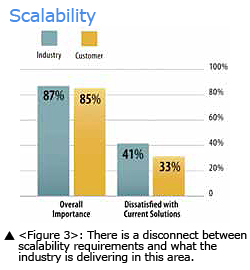 TCO is the No.1 driver influencing the physical access control market according to the Avisian study. Increasingly, customers are looking beyond installation costs to base purchase decisions on TCO or operational expenses. There are several key life cycle management issues to consider, including the equipment's expected useful life, how it will depreciate over time, and the technology's migration path.
TCO is the No.1 driver influencing the physical access control market according to the Avisian study. Increasingly, customers are looking beyond installation costs to base purchase decisions on TCO or operational expenses. There are several key life cycle management issues to consider, including the equipment's expected useful life, how it will depreciate over time, and the technology's migration path.
The economy is obviously forcing more justification of expenditures, and companies also need to factor maintenance, upgrades and ROI into their cost calculations. Meanwhile, product life cycles are shrinking, as illustrated by the accelerated introduction of high-frequency technologies and associated government standards and protocol requirements. Customers must leverage existing investments (per Figure 3, 90 percent of the respondents said this was important, and 50 percent were dissatisfied in this area). Respondents also said they wanted interoperability or ease of migration, portability of identities to new security models, and scalable solutions.
Sustainability
One last future-proofing consideration is sustainability, as the industry begins exploring how to drive new building automation solutions for energy management. Although today's implementations are limited, we get a sense of what's coming by looking at early industry influencers, emerging standards and signs that cost barriers are beginning to come down. The US government's ICMA Green Task Force is already looking at how to “green” factories and institute “eco labeling” at the manufacturer level. There is growing discussion around energy management via access control and how to integrate the two. We also can learn by studying other industries and how they have adopted and leveraged Leadership in Energy and Environmental Design (LEED) standards.
Balancing the Equation
Despite new market dynamics, the three core elements of the customer value equation — cost, security and convenience — continue to fuel drivers for change in the physical access control space as increased convenience, lower TCO and achieving higher levels of security continue to dictate market development. At the same time, new dynamics related to government influence, technology trends, security requirements, single-card application convergence and TCO are creating new opportunities to better serve customers' needs, as we help them balance their value equation for physical access control solutions.